Colossus Computer on:
[Wikipedia]
[Google]
[Amazon]
Colossus was a set of

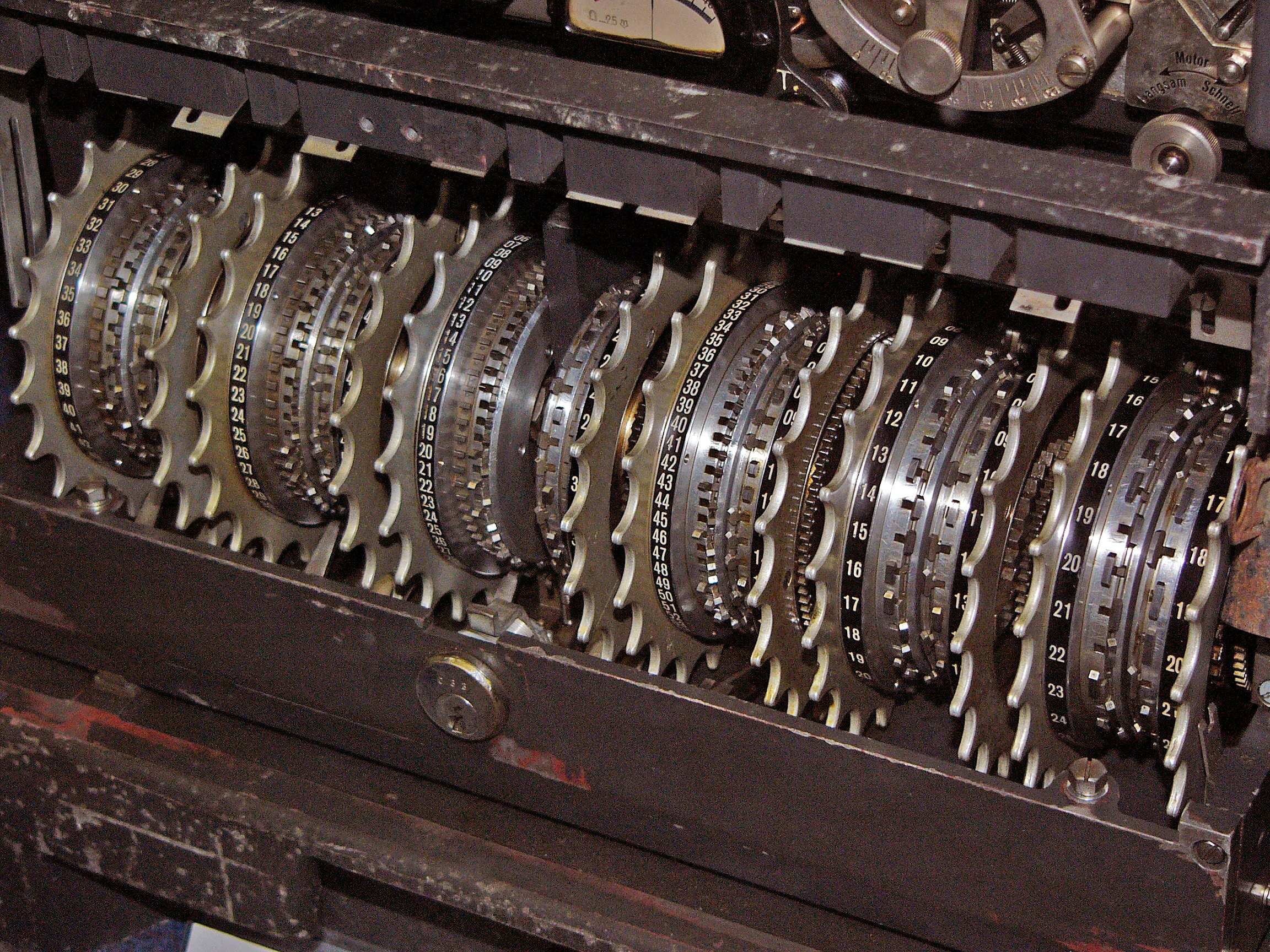 The Colossus computers were used to help decipher intercepted radio
The Colossus computers were used to help decipher intercepted radio  With a sufficiently random keystream, a Vernam cipher removes the natural language property of a plaintext message of having an uneven
With a sufficiently random keystream, a Vernam cipher removes the natural language property of a plaintext message of having an uneven
 The main units of the Mark 2 design were as follows.
* A tape transport with an 8-photocell reading mechanism.
* A six character FIFO
The main units of the Mark 2 design were as follows.
* A tape transport with an 8-photocell reading mechanism.
* A six character FIFO
 The Newmanry was staffed by cryptanalysts, operators from the Women's Royal Naval Service (WRNS) – known as "Wrens" – and engineers who were permanently on hand for maintenance and repair. By the end of the war the staffing was 272 Wrens and 27 men.
The first job in operating Colossus for a new message was to prepare the paper tape loop. This was performed by the Wrens who stuck the two ends together using
The Newmanry was staffed by cryptanalysts, operators from the Women's Royal Naval Service (WRNS) – known as "Wrens" – and engineers who were permanently on hand for maintenance and repair. By the end of the war the staffing was 272 Wrens and 27 men.
The first job in operating Colossus for a new message was to prepare the paper tape loop. This was performed by the Wrens who stuck the two ends together using

 Howard Campaigne, a mathematician and cryptanalyst from the US Navy's
Howard Campaigne, a mathematician and cryptanalyst from the US Navy's
 Construction of a fully functional rebuild of a Colossus Mark 2 was undertaken between 1993 and 2008 by a team led by Tony Sale. In spite of the blueprints and hardware being destroyed, a surprising amount of material survived, mainly in engineers' notebooks, but a considerable amount of it in the U.S. The optical tape reader might have posed the biggest problem, but Dr. Arnold Lynch, its original designer was able to redesign it to his own original specification. The reconstruction is on display, in the historically correct place for Colossus No. 9, at
Construction of a fully functional rebuild of a Colossus Mark 2 was undertaken between 1993 and 2008 by a team led by Tony Sale. In spite of the blueprints and hardware being destroyed, a surprising amount of material survived, mainly in engineers' notebooks, but a considerable amount of it in the U.S. The optical tape reader might have posed the biggest problem, but Dr. Arnold Lynch, its original designer was able to redesign it to his own original specification. The reconstruction is on display, in the historically correct place for Colossus No. 9, at
Early computer development
The National Museum of Computing (TNMOC)
*
TNMOC: The 75th anniversary of the first attack
Contains a great deal of information, including: *
*
**
**
**
**
A detailed tour of the replica Colossus – make sure to click on the "More Text" links on each image to see the informative detailed text about that part of Colossus *
IEEE lecture
– Transcript of a lecture Tony Sale gave describing the reconstruction project
BBC news article reporting on the replica Colossus
BBC news article: "Colossus cracks codes once more"
BBC news article: BBC news article: "Bletchley's code-cracking Colossus" with video interviews 2010-02-02
with much information and links to recently declassified information
Was the Manchester Baby conceived at Bletchley Park?
*
online virtual simulation of Colossus
{{Mainframes 1940s computers Early British computers Bletchley Park Cryptanalytic devices Military computers Vacuum tube computers World War II British electronics English inventions Computer-related introductions in 1943 Computer-related introductions in 1944 Computer-related introductions in 1945 Serial computers
computer
A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as C ...
s developed by British codebreakers
Cryptanalysis (from the Greek language, Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach C ...
in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher
Cryptanalysis of the Lorenz cipher was the process that enabled the British to read high-level German army messages during World War II. The British Government Code and Cypher School (GC&CS) at Bletchley Park decrypted many communications betwee ...
. Colossus used thermionic valves (vacuum tubes) to perform Boolean and counting operations. Colossus is thus regarded as the world's first programmable, electronic
Electronic may refer to:
*Electronics, the science of how to control electric energy in semiconductor
* ''Electronics'' (magazine), a defunct American trade journal
*Electronic storage, the storage of data using an electronic device
*Electronic co ...
, digital computer, although it was programmed by switches and plugs and not by a stored program
A stored-program computer is a computer that stores program instructions in electronically or optically accessible memory. This contrasts with systems that stored the program instructions with plugboards or similar mechanisms.
The definition ...
.
Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers
Thomas Harold Flowers MBE (22 December 1905 – 28 October 1998) was an English engineer with the British General Post Office. During World War II, Flowers designed and built Colossus, the world's first programmable electronic computer, to help ...
to solve a problem posed by mathematician Max Newman
Maxwell Herman Alexander Newman, FRS, (7 February 1897 – 22 February 1984), generally known as Max Newman, was a British mathematician and codebreaker. His work in World War II led to the construction of Colossus, the world's first operatio ...
at the Government Code and Cypher School
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the Uni ...
(GC&CS) at Bletchley Park
Bletchley Park is an English country house and estate in Bletchley, Milton Keynes ( Buckinghamshire) that became the principal centre of Allied code-breaking during the Second World War. The mansion was constructed during the years following ...
. Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical co ...
's use of probability in cryptanalysis (see Banburismus
Banburismus was a cryptanalytic process developed by Alan Turing at Bletchley Park in Britain during the Second World War. It was used by Bletchley Park's Hut 8 to help break German ''Kriegsmarine'' (naval) messages enciphered on Enigma machin ...
) contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies in World War II to read substantial amounts of Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military in ...
. (Turing's machine that helped decode Enigma
Enigma may refer to:
*Riddle, someone or something that is mysterious or puzzling
Biology
*ENIGMA, a class of gene in the LIM domain
Computing and technology
* Enigma (company), a New York-based data-technology startup
* Enigma machine, a family ...
was the electromechanical Bombe
The bombe () was an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II. The US Navy and US Army later produced their own machines to the same functi ...
, not Colossus.)
The prototype, Colossus Mark 1, was shown to be working in December 1943 and was in use at Bletchley Park by early 1944. An improved Colossus Mark 2 that used shift register
A shift register is a type of digital circuit using a cascade of flip-flops where the output of one flip-flop is connected to the input of the next. They share a single clock signal, which causes the data stored in the system to shift from one loc ...
s to quintuple the processing speed, first worked on 1 June 1944, just in time for the Normandy landings
The Normandy landings were the landing operations and associated airborne operations on Tuesday, 6 June 1944 of the Allied invasion of Normandy in Operation Overlord during World War II. Codenamed Operation Neptune and often referred to as ...
on D-Day. Ten Colossi were in use by the end of the war and an eleventh was being commissioned. Bletchley Park's use of these machines allowed the Allies
An alliance is a relationship among people, groups, or states that have joined together for mutual benefit or to achieve some common purpose, whether or not explicit agreement has been worked out among them. Members of an alliance are called ...
to obtain a vast amount of high-level military intelligence
Military intelligence is a military discipline that uses information collection and analysis approaches to provide guidance and direction to assist commanders in their decisions. This aim is achieved by providing an assessment of data from a ...
from intercepted radiotelegraphy messages between the German High Command (''OKW'') and their army
An army (from Old French ''armee'', itself derived from the Latin verb ''armāre'', meaning "to arm", and related to the Latin noun ''arma'', meaning "arms" or "weapons"), ground force or land force is a fighting force that fights primarily on ...
commands throughout occupied Europe.
The existence of the Colossus machines was kept secret until the mid-1970s. All but two machines were dismantled into such small parts that their use could not be inferred. The two retained machines were eventually dismantled in the 1960s. A functioning rebuild of a Mark 2 Colossus was completed in 2008 by Tony Sale
Tony may refer to:
People and fictional characters
* Tony (given name), including a list of people and fictional characters
* Gregory Tony (born 1978), American law enforcement officer
* Motu Tony (born 1981), New Zealand international rugby leag ...
and a team of volunteers; it is on display at The National Museum of Computing
The National Museum of Computing is a museum in the United Kingdom dedicated to collecting and restoring historic computer systems. The museum is based in rented premises at Bletchley Park in Milton Keynes, Buckinghamshire and opened in 2007. ...
on Bletchley Park
Bletchley Park is an English country house and estate in Bletchley, Milton Keynes ( Buckinghamshire) that became the principal centre of Allied code-breaking during the Second World War. The mansion was constructed during the years following ...
.
Purpose and origins

 The Colossus computers were used to help decipher intercepted radio
The Colossus computers were used to help decipher intercepted radio teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point and point-to-multipoint configurations. Initia ...
messages that had been encrypted
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can deci ...
using an unknown device. Intelligence information revealed that the Germans called the wireless teleprinter transmission systems ''"Sägefisch"'' (sawfish). This led the British to call encrypted German teleprinter traffic "Fish
Fish are aquatic, craniate, gill-bearing animals that lack limbs with digits. Included in this definition are the living hagfish, lampreys, and cartilaginous and bony fish as well as various extinct related groups. Approximately 95% of li ...
", and the unknown machine and its intercepted messages " Tunny" (tunafish).
Before the Germans increased the security of their operating procedures, British cryptanalysts diagnosed how the unseen machine functioned and built an imitation of it called " British Tunny".
It was deduced that the machine had twelve wheels and used a Vernam cipher
Vernam is a surname. Notable people with the surname include:
*Charles Vernam (born 1996), English professional footballer
*Gilbert Vernam (1890–1960), invented an additive polyalphabetic stream cipher and later co-invented an automated one-time ...
ing technique on message characters in the standard 5-bit ITA2
The Baudot code is an early character encoding for telegraphy invented by Émile Baudot in the 1870s. It was the predecessor to the International Telegraph Alphabet No. 2 (ITA2), the most common teleprinter code in use until the advent of ASCII ...
telegraph code. It did this by combining the plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of com ...
characters with a stream of key
Key or The Key may refer to:
Common meanings
* Key (cryptography), a piece of information that controls the operation of a cryptography algorithm
* Key (lock), device used to control access to places or facilities restricted by a lock
* Key (map ...
characters using the XOR Boolean function
In mathematics, a Boolean function is a function whose arguments and result assume values from a two-element set (usually , or ). Alternative names are switching function, used especially in older computer science literature, and truth function ...
to produce the ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
.
In August 1941, a blunder by German operators led to the transmission of two versions of the same message with identical machine settings. These were intercepted and worked on at Bletchley Park. First, John Tiltman
Brigadier John Hessell Tiltman, (25 May 1894 – 10 August 1982) was a British Army officer who worked in intelligence, often at or with the Government Code and Cypher School (GC&CS) starting in the 1920s. His intelligence work was largely conn ...
, a very talented GC&CS cryptanalyst, derived a key stream of almost 4000 characters. Then Bill Tutte
William Thomas Tutte OC FRS FRSC (; 14 May 1917 – 2 May 2002) was an English and Canadian codebreaker and mathematician. During the Second World War, he made a brilliant and fundamental advance in cryptanalysis of the Lorenz cipher, a majo ...
, a newly arrived member of the Research Section, used this keystream to work out the logical structure of the Lorenz machine. He deduced that the twelve wheels consisted of two groups of five, which he named the χ (''chi
Chi or CHI may refer to:
Greek
*Chi (letter), the Greek letter (uppercase Χ, lowercase χ);
Chinese
*Chi (length), ''Chi'' (length) (尺), a traditional unit of length, about ⅓ meter
*Chi (mythology) (螭), a dragon
*Chi (surname) (池, pin ...
'') and ψ (''psi
Psi, PSI or Ψ may refer to:
Alphabetic letters
* Psi (Greek) (Ψ, ψ), the 23rd letter of the Greek alphabet
* Psi (Cyrillic) (Ѱ, ѱ), letter of the early Cyrillic alphabet, adopted from Greek
Arts and entertainment
* "Psi" as an abbreviatio ...
'') wheels, the remaining two he called μ ('' mu'') or "motor" wheels. The ''chi'' wheels stepped regularly with each letter that was encrypted, while the ''psi'' wheels stepped irregularly, under the control of the motor wheels.
 With a sufficiently random keystream, a Vernam cipher removes the natural language property of a plaintext message of having an uneven
With a sufficiently random keystream, a Vernam cipher removes the natural language property of a plaintext message of having an uneven frequency distribution
In statistics, the frequency (or absolute frequency) of an event i is the number n_i of times the observation has occurred/recorded in an experiment or study. These frequencies are often depicted graphically or in tabular form.
Types
The cumula ...
of the different characters, to produce a uniform distribution in the ciphertext. The Tunny machine did this well. However, the cryptanalysts worked out that by examining the frequency distribution of the character-to-character changes in the ciphertext, instead of the plain characters, there was a departure from uniformity which provided a way into the system. This was achieved by "differencing" in which each bit or character was XOR-ed with its successor. After Germany surrendered, allied forces captured a Tunny machine and discovered that it was the electromechanical
In engineering, electromechanics combines processes and procedures drawn from electrical engineering and mechanical engineering. Electromechanics focuses on the interaction of electrical and mechanical systems as a whole and how the two systems ...
Lorenz SZ (''Schlüsselzusatzgerät'', cipher attachment) in-line cipher machine.
In order to decrypt the transmitted messages, two tasks had to be performed. The first was "wheel breaking", which was the discovery of the cam patterns for all the wheels. These patterns were set up on the Lorenz machine and then used for a fixed period of time for a succession of different messages. Each transmission, which often contained more than one message, was enciphered with a different start position of the wheels. Alan Turing invented a method of wheel-breaking that became known as Turingery
Turingery in ''Testery Methods 1942–1944'' or Turing's method (playfully dubbed Turingismus by Peter Ericsson, Peter Hilton and Donald Michie) was a manual codebreaking method devised in July 1942 by the mathematician and cryptanalyst Alan Turi ...
. Turing's technique was further developed into "Rectangling", for which Colossus could produce tables for manual analysis. Colossi 2, 4, 6, 7 and 9 had a "gadget" to aid this process.
The second task was "wheel setting", which worked out the start positions of the wheels for a particular message and could only be attempted once the cam patterns were known. It was this task for which Colossus was initially designed. To discover the start position of the ''chi'' wheels for a message, Colossus compared two character streams, counting statistics from the evaluation of programmable Boolean functions. The two streams were the ciphertext, which was read at high speed from a paper tape, and the keystream, which was generated internally, in a simulation of the unknown German machine. After a succession of different Colossus runs to discover the likely ''chi''-wheel settings, they were checked by examining the frequency distribution of the characters in the processed ciphertext. Colossus produced these frequency counts.
Decryption processes
By using differencing and knowing that the ''psi'' wheels did not advance with each character, Tutte worked out that trying just two differenced bits (impulses) of the ''chi''-stream against the differenced ciphertext would produce a statistic that was non-random. This became known as Tutte's "1+2 break in". It involved calculating the following Boolean function: ::: and counting the number of times it yielded "false" (zero). If this number exceeded a pre-defined threshold value known as the "set total", it was printed out. The cryptanalyst would examine the printout to determine which of the putative start positions was most likely to be the correct one for the ''chi''-1 and ''chi''-2 wheels. This technique would then be applied to other pairs of, or single, impulses to determine the likely start position of all five ''chi'' wheels. From this, the de-''chi'' (D) of a ciphertext could be obtained, from which the ''psi'' component could be removed by manual methods. If the frequency distribution of characters in the de-''chi'' version of the ciphertext was within certain bounds, "wheel setting" of the ''chi'' wheels was considered to have been achieved, and the message settings and de-''chi'' were passed to the "Testery
The Testery was a section at Bletchley Park, the British codebreaking station during World War II. It was set up in July 1942 as the "FISH Subsection" under Major Ralph Tester, hence its alternative name. Four founder members were Tester himself ...
". This was the section at Bletchley Park led by Major Ralph Tester
Ralph Paterson Tester (2 June 1902 – May 1998) was an administrator at Bletchley Park, the British codebreaking station during World War II. He founded and supervised a section named the ''Testery'' for breaking Tunny (a Fish cipher).
Backgroun ...
where the bulk of the decrypting work was done by manual and linguistic methods.
Colossus could also derive the start position of the ''psi'' and motor wheels, but this was not much done until the last few months of the war when there were plenty of Colossi available and the number of Tunny messages had declined.
Design and construction
Colossus was developed for the "Newmanry
The Newmanry was a section at Bletchley Park, the British codebreaking station during World War II. Its job was to develop and employ statistical and machine methods in cryptanalysis of the Lorenz cipher. It worked very closely with the Testery wh ...
", the section headed by the mathematician Max Newman
Maxwell Herman Alexander Newman, FRS, (7 February 1897 – 22 February 1984), generally known as Max Newman, was a British mathematician and codebreaker. His work in World War II led to the construction of Colossus, the world's first operatio ...
that was responsible for machine methods against the twelve-rotor Lorenz SZ40/42 on-line teleprinter cipher machine (code-named Tunny, for tunafish). The Colossus design arose out of a prior project that produced a counting machine dubbed "Heath Robinson
William Heath Robinson (31 May 1872 – 13 September 1944) was an English cartoonist, illustrator and artist, best known for drawings of whimsically elaborate machines to achieve simple objectives.
In the UK, the term "Heath Robinson cont ...
". Although it proved the concept of machine analysis for this part of the process, it was initially unreliable. The electro-mechanical parts were relatively slow and it was difficult to synchronise two looped paper tapes, one containing the enciphered message, and the other representing part of the keystream of the Lorenz machine, also the tapes tended to stretch when being read at up to 2000 characters per second.
Tommy Flowers MBE Mbe may refer to:
* Mbé, a town in the Republic of the Congo
* Mbe Mountains Community Forest, in Nigeria
* Mbe language, a language of Nigeria
* Mbe' language, language of Cameroon
* ''mbe'', ISO 639 code for the extinct Molala language
Molal ...
was a senior electrical engineer and Head of the Switching Group at the Post Office Research Station
The Post Office Research Station was first established as a separate section of the General Post Office in 1909.
In 1921, the Research Station moved to Dollis Hill, north west London, initially in ex-army huts.
The main permanent buildings at ...
at Dollis Hill
Dollis Hill is an area in northwest London, which consists of the streets surrounding the 35 hectares (86 acres) Gladstone Park. It is served by a London Underground station, Dollis Hill, on the Jubilee line, providing good links to central Lo ...
. Prior to his work on Colossus, he had been involved with GC&CS at Bletchley Park from February 1941 in an attempt to improve the Bombe
The bombe () was an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II. The US Navy and US Army later produced their own machines to the same functi ...
s that were used in the cryptanalysis of the German Enigma cipher machine. He was recommended to Max Newman by Alan Turing, who had been impressed by his work on the Bombes. The main components of the Heath Robinson machine were as follows.
* A tape transport and reading mechanism that ran the looped key and message tapes at between 1000 and 2000 characters per second.
* A combining unit that implemented the logic of Tutte's method.
* A counting unit that had been designed by C. E. Wynn-Williams
Charles Eryl Wynn-Williams (5 March 1903 – 30 August 1979), was a Welsh physicist, noted for his research on electronic instrumentation for use in nuclear physics. His work on the scale-of-two counter contributed to the development of the moder ...
of the Telecommunications Research Establishment
The Telecommunications Research Establishment (TRE) was the main United Kingdom research and development organization for radio navigation, radar, infra-red detection for heat seeking missiles, and related work for the Royal Air Force (RAF) ...
(TRE) at Malvern, which counted the number of times the logical function returned a specified truth value
In logic and mathematics, a truth value, sometimes called a logical value, is a value indicating the relation of a proposition to truth, which in classical logic has only two possible values (''true'' or '' false'').
Computing
In some progr ...
.
Flowers had been brought in to design the Heath Robinson's combining unit. He was not impressed by the system of a key tape that had to be kept synchronised with the message tape and, on his own initiative, he designed an electronic machine which eliminated the need for the key tape by having an electronic analogue of the Lorenz (Tunny) machine. He presented this design to Max Newman in February 1943, but the idea that the one to two thousand thermionic valves (vacuum tube
A vacuum tube, electron tube, valve (British usage), or tube (North America), is a device that controls electric current flow in a high vacuum between electrodes to which an electric voltage, potential difference has been applied.
The type kn ...
s and thyratron
A thyratron is a type of gas-filled tube used as a high-power electrical switch and controlled rectifier. Thyratrons can handle much greater currents than similar hard-vacuum tubes. Electron multiplication occurs when the gas becomes ionized, p ...
s) proposed, could work together reliably, was greeted with great scepticism, so more Robinsons were ordered from Dollis Hill. Flowers, however, knew from his pre-war work that most thermionic valve failures occurred as a result of the thermal stresses at power-up, so not powering a machine down reduced failure rates to very low levels. Additionally, if the heaters were started at a low voltage then slowly brought up to full voltage, thermal stress was reduced. The valves themselves could be soldered-in to avoid problems with plug-in bases, which could be unreliable. Flowers persisted with the idea and obtained support from the Director of the Research Station, W Gordon Radley.
Flowers and his team of some fifty people in the switching group spent eleven months from early February 1943 designing and building a machine that dispensed with the second tape of the Heath Robinson, by generating the wheel patterns electronically. Flowers used some of his own money for the project. This prototype, Mark 1 Colossus, contained 1,600 thermionic valves (tubes). It performed satisfactorily at Dollis Hill on 8 December 1943 and was dismantled and shipped to Bletchley Park, where it was delivered on 18 January and re-assembled by Harry Fensom and Don Horwood. It was operational in January and it successfully attacked its first message on 5 February 1944. It was a large structure and was dubbed 'Colossus', supposedly by the WRNS operators. However, a memo held in the National Archives written by Max Newman on 18 January 1944 records that 'Colossus arrives today".
During the development of the prototype, an improved design had been developed – the Mark 2 Colossus. Four of these were ordered in March 1944 and by the end of April the number on order had been increased to twelve. Dollis Hill was put under pressure to have the first of these working by 1 June. Allen Coombs took over leadership of the production Mark 2 Colossi, the first of which – containing 2,400 valves – became operational at 08:00 on 1 June 1944, just in time for the Allied Invasion of Normandy
Operation Overlord was the codename for the Battle of Normandy, the Allied operation that launched the successful invasion of German-occupied Western Europe during World War II. The operation was launched on 6 June 1944 (D-Day) with the Norm ...
on D-Day
The Normandy landings were the landing operations and associated airborne operations on Tuesday, 6 June 1944 of the Allied invasion of Normandy in Operation Overlord during World War II. Codenamed Operation Neptune and often referred to as D ...
. Subsequently, Colossi were delivered at the rate of about one a month. By the time of V-E Day
Victory in Europe Day is the day celebrating the formal acceptance by the Allies of World War II of Germany's unconditional surrender of its armed forces on Tuesday, 8 May 1945, marking the official end of World War II in Europe in the Easte ...
there were ten Colossi working at Bletchley Park and a start had been made on assembling an eleventh.
 The main units of the Mark 2 design were as follows.
* A tape transport with an 8-photocell reading mechanism.
* A six character FIFO
The main units of the Mark 2 design were as follows.
* A tape transport with an 8-photocell reading mechanism.
* A six character FIFO shift register
A shift register is a type of digital circuit using a cascade of flip-flops where the output of one flip-flop is connected to the input of the next. They share a single clock signal, which causes the data stored in the system to shift from one loc ...
.
* Twelve thyratron ring stores that simulated the Lorenz machine generating a bit-stream for each wheel.
* Panels of switches for specifying the program and the "set total".
* A set of functional units that performed Boolean operations.
* A "span counter" that could suspend counting for part of the tape.
* A master control that handled clocking, start and stop signals, counter readout and printing.
* Five electronic counters.
* An electric typewriter.
Most of the design of the electronics was the work of Tommy Flowers, assisted by William Chandler, Sidney Broadhurst and Allen Coombs; with Erie Speight and Arnold Lynch developing the photoelectric reading mechanism. Coombs remembered Flowers, having produced a rough draft of his design, tearing it into pieces that he handed out to his colleagues for them to do the detailed design and get their team to manufacture it. The Mark 2 Colossi were both five times faster and were simpler to operate than the prototype.
Data input to Colossus was by photoelectric
The photoelectric effect is the emission of electrons when electromagnetic radiation, such as light, hits a material. Electrons emitted in this manner are called photoelectrons. The phenomenon is studied in condensed matter physics, and solid sta ...
reading of a paper tape transcription of the enciphered intercepted message. This was arranged in a continuous loop so that it could be read and re-read multiple times – there being no internal storage for the data. The design overcame the problem of synchronizing the electronics with the speed of the message tape by generating a clock signal from reading its sprocket holes. The speed of operation was thus limited by the mechanics of reading the tape. During development, the tape reader was tested up to 9700 characters per second (53 mph) before the tape disintegrated. So 5000 characters/second () was settled on as the speed for regular use. Flowers designed a 6-character shift register, which was used both for computing the delta function (ΔZ) and for testing five different possible starting points of Tunny's wheels in the five processors. This five-way parallelism enabled five simultaneous tests and counts to be performed giving an effective processing speed of 25,000 characters per second. The computation used algorithms devised by W. T. Tutte
William Thomas Tutte OC FRS FRSC (; 14 May 1917 – 2 May 2002) was an English and Canadian codebreaker and mathematician. During the Second World War, he made a brilliant and fundamental advance in cryptanalysis of the Lorenz cipher, a majo ...
and colleagues to decrypt a Tunny message.
Operation
 The Newmanry was staffed by cryptanalysts, operators from the Women's Royal Naval Service (WRNS) – known as "Wrens" – and engineers who were permanently on hand for maintenance and repair. By the end of the war the staffing was 272 Wrens and 27 men.
The first job in operating Colossus for a new message was to prepare the paper tape loop. This was performed by the Wrens who stuck the two ends together using
The Newmanry was staffed by cryptanalysts, operators from the Women's Royal Naval Service (WRNS) – known as "Wrens" – and engineers who were permanently on hand for maintenance and repair. By the end of the war the staffing was 272 Wrens and 27 men.
The first job in operating Colossus for a new message was to prepare the paper tape loop. This was performed by the Wrens who stuck the two ends together using Bostik
Bostik is a manufacturer and distributor of adhesives and sealants for the construction, industrial and consumer markets. With annual sales of €2.1 billion, the company employs 6,000 people and has a presence in more than 40 countries. Bo ...
glue, ensuring that there was a 150-character length of blank tape between the end and the start of the message. Using a special hand punch they inserted a start hole between the third and fourth channels sprocket holes from the end of the blank section, and a stop hole between the fourth and fifth channels sprocket holes from the end of the characters of the message. These were read by specially positioned photocells and indicated when the message was about to start and when it ended. The operator would then thread the paper tape through the gate and around the pulleys of the bedstead and adjust the tension. The two-tape bedstead design had been carried on from Heath Robinson so that one tape could be loaded whilst the previous one was being run. A switch on the Selection Panel specified the "near" or the "far" tape.
After performing various resetting and zeroizing tasks, the Wren operators would, under instruction from the cryptanalyst, operate the "set total" decade switches and the K2 panel switches to set the desired algorithm. They would then start the bedstead tape motor and lamp and, when the tape was up to speed, operate the master start switch.
Programming

 Howard Campaigne, a mathematician and cryptanalyst from the US Navy's
Howard Campaigne, a mathematician and cryptanalyst from the US Navy's OP-20-G
OP-20-G or "Office of Chief Of Naval Operations (OPNAV), 20th Division of the Office of Naval Communications, G Section / Communications Security", was the U.S. Navy's signals intelligence and cryptanalysis group during World War II. Its mission ...
, wrote the following in a foreword to Flowers' 1983 paper "The Design of Colossus".
Colossus was not a stored-program computer
A stored-program computer is a computer that stores program instructions in electronically or optically accessible memory. This contrasts with systems that stored the program instructions with plugboards or similar mechanisms.
The definition i ...
. The input data for the five parallel processors was read from the looped message paper tape and the electronic pattern generators for the ''chi'', ''psi'' and motor wheels. The programs for the processors were set and held on the switches and jack panel connections. Each processor could evaluate a Boolean function and count and display the number of times it yielded the specified value of "false" (0) or "true" (1) for each pass of the message tape.
Input to the processors came from two sources, the shift registers from tape reading and the thyratron rings that emulated the wheels of the Tunny machine. The characters on the paper tape were called Z and the characters from the Tunny emulator were referred to by the Greek letters that Bill Tutte had given them when working out the logical structure of the machine. On the selection panel, switches specified either Z or ΔZ, either or Δ and either or Δ for the data to be passed to the jack field and 'K2 switch panel'. These signals from the wheel simulators could be specified as stepping on with each new pass of the message tape or not.
The K2 switch panel had a group of switches on the left-hand side to specify the algorithm. The switches on the right-hand side selected the counter to which the result was fed. The plugboard allowed less specialized conditions to be imposed. Overall the K2 switch panel switches and the plugboard allowed about five billion different combinations of the selected variables.
As an example: a set of runs for a message tape might initially involve two ''chi'' wheels, as in Tutte's 1+2 algorithm. Such a two-wheel run was called a long run, taking on average eight minutes unless the parallelism was utilised to cut the time by a factor of five. The subsequent runs might only involve setting one ''chi'' wheel, giving a short run taking about two minutes. Initially, after the initial long run, the choice of the next algorithm to be tried was specified by the cryptanalyst. Experience showed, however, that decision trees for this iterative process could be produced for use by the Wren operators in a proportion of cases.
Influence and fate
Although the Colossus was the first of the electronic digital machines with programmability, albeit limited by modern standards, it was not a general-purpose machine, being designed for a range of cryptanalytic tasks, most involving counting the results of evaluating Boolean algorithms. A Colossus computer was thus not a fullyTuring complete
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical co ...
machine. However, University of San Francisco
The University of San Francisco (USF) is a private Jesuit university in San Francisco, California. The university's main campus is located on a setting between the Golden Gate Bridge and Golden Gate Park. The main campus is nicknamed "The Hil ...
professor Benjamin Wells has shown that if all ten Colossus machines made were rearranged in a specific cluster
may refer to:
Science and technology Astronomy
* Cluster (spacecraft), constellation of four European Space Agency spacecraft
* Asteroid cluster, a small asteroid family
* Cluster II (spacecraft), a European Space Agency mission to study t ...
, then the entire set of computers could have simulated a universal Turing machine
In computer science, a universal Turing machine (UTM) is a Turing machine that can simulate an arbitrary Turing machine on arbitrary input. The universal machine essentially achieves this by reading both the description of the machine to be simu ...
, and thus be Turing complete.
Colossus and the reasons for its construction were highly secret and remained so for 30 years after the War. Consequently, it was not included in the history of computing hardware for many years, and Flowers and his associates were deprived of the recognition they were due. Colossi 1 to 10 were dismantled after the war and parts returned to the Post Office. Some parts, sanitised as to their original purpose, were taken to Max Newman's Royal Society
The Royal Society, formally The Royal Society of London for Improving Natural Knowledge, is a learned society and the United Kingdom's national academy of sciences. The society fulfils a number of roles: promoting science and its benefits, re ...
Computing Machine Laboratory
The Computing Machine Laboratory at the University of Manchester in the north of England was established by Max Newman shortly after the end of World War II, around 1946.
The Laboratory was funded through a grant from the Royal Society, which was ...
at Manchester University
, mottoeng = Knowledge, Wisdom, Humanity
, established = 2004 – University of Manchester Predecessor institutions: 1956 – UMIST (as university college; university 1994) 1904 – Victoria University of Manchester 1880 – Victoria Univer ...
. Tommy Flowers was ordered to destroy all documentation and burnt them in a furnace at Dollis Hill. He later said of that order:
Colossi 11 and 12, along with two replica Tunny machines, were retained, being moved to GCHQ
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the Uni ...
's new headquarters at Eastcote
Eastcote is a suburban area in the London Borough of Hillingdon, in northwest London.
In the Middle Ages, Eastcote was one of the three areas that made up the parish of Ruislip, under the name of Ascot. The name came from its position to the e ...
in April 1946, and again with GCHQ to Cheltenham between 1952 and 1954. One of the Colossi, known as ''Colossus Blue'', was dismantled in 1959; the other in 1960. There had been attempts to adapt them to other purposes, with varying success; in their later years they had been used for training. Jack Good related how he was the first to use Colossus after the war, persuading the US National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
that it could be used to perform a function for which they were planning to build a special-purpose machine. Colossus was also used to perform character counts on one-time pad
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is not smaller than the message being sent. In this technique, a plaintext is paired with a ran ...
tape to test for non-randomness.
A small number of people who were associated with Colossus—and knew that large-scale, reliable, high-speed electronic digital computing devices were feasible—played significant roles in early computer work in the UK and probably in the US. However, being so secret, it had little direct influence on the development of later computers; it was EDVAC that was the seminal computer architecture of the time. In 1972, Herman Goldstine, who was unaware of Colossus and its legacy to the projects of people such as Alan Turing (ACE
An ace is a playing card, die or domino with a single pip. In the standard French deck, an ace has a single suit symbol (a heart, diamond, spade, or club) located in the middle of the card, sometimes large and decorated, especially in the c ...
), Max Newman (Manchester computers
The Manchester computers were an innovative series of stored-program electronic computers developed during the 30-year period between 1947 and 1977 by a small team at the University of Manchester, under the leadership of Tom Kilburn. They includ ...
) and Harry Huskey
Harry Douglas Huskey (January 19, 1916 – April 9, 2017) was an American computer design pioneer.
Early life and career
Huskey was born in Whittier, in the Smoky Mountains region of North Carolina and grew up in Idaho. He received his bache ...
(Bendix G-15
The Bendix G-15 is a computer introduced in 1956 by the Bendix Corporation, Computer Division, Los Angeles, California. It is about and weighs about . The G-15 has a drum memory of 2,160 29-bit words, along with 20 words used for special purpos ...
), wrote that,
Professor Brian Randell
Brian Randell (born 1936) is a British computer scientist, and Emeritus Professor at the School of Computing, Newcastle University, United Kingdom. He specialises in research into software fault tolerance and dependability, and is a noted aut ...
, who unearthed information about Colossus in the 1970s, commented on this, saying that:
Randell's efforts started to bear fruit in the mid-1970s. The secrecy about Bletchley Park had been broken when Group Captain Winterbotham published his book ''The Ultra Secret'' in 1974. Randell was researching the history of computer science in Britain for a conference on the history of computing held at the Los Alamos Scientific Laboratory, New Mexico on 10-15 June 1976, and got permission to present a paper on wartime development of the COLOSSI at the Post Office Research Station
The Post Office Research Station was first established as a separate section of the General Post Office in 1909.
In 1921, the Research Station moved to Dollis Hill, north west London, initially in ex-army huts.
The main permanent buildings at ...
, Dollis Hill (in October 1975 the British Government had released a series of captioned photographs from the Public Record Office). The interest in the “revelations” in his paper resulted in a special evening meeting when Randell and Cooombs answered further questions. Coombs later wrote that ''no member of our team could ever forget the fellowship, the sense of purpose and, above all, the breathless excitement of those days''. In 1977 Randell published an article ''The First Electronic Computer'' in several journals.
In October 2000, a 500-page technical report on the Tunny cipher and its cryptanalysis—entitled ''General Report on Tunny''—was released by GCHQ to the national Public Record Office
The Public Record Office (abbreviated as PRO, pronounced as three letters and referred to as ''the'' PRO), Chancery Lane in the City of London, was the guardian of the national archives of the United Kingdom from 1838 until 2003, when it was m ...
, and it contains a fascinating paean
A paean () is a song or lyric poem expressing triumph or thanksgiving. In classical antiquity, it is usually performed by a chorus, but some examples seem intended for an individual voice ( monody). It comes from the Greek παιάν (also πα ...
to Colossus by the cryptographers who worked with it:
Reconstruction
 Construction of a fully functional rebuild of a Colossus Mark 2 was undertaken between 1993 and 2008 by a team led by Tony Sale. In spite of the blueprints and hardware being destroyed, a surprising amount of material survived, mainly in engineers' notebooks, but a considerable amount of it in the U.S. The optical tape reader might have posed the biggest problem, but Dr. Arnold Lynch, its original designer was able to redesign it to his own original specification. The reconstruction is on display, in the historically correct place for Colossus No. 9, at
Construction of a fully functional rebuild of a Colossus Mark 2 was undertaken between 1993 and 2008 by a team led by Tony Sale. In spite of the blueprints and hardware being destroyed, a surprising amount of material survived, mainly in engineers' notebooks, but a considerable amount of it in the U.S. The optical tape reader might have posed the biggest problem, but Dr. Arnold Lynch, its original designer was able to redesign it to his own original specification. The reconstruction is on display, in the historically correct place for Colossus No. 9, at The National Museum of Computing
The National Museum of Computing is a museum in the United Kingdom dedicated to collecting and restoring historic computer systems. The museum is based in rented premises at Bletchley Park in Milton Keynes, Buckinghamshire and opened in 2007. ...
, in H Block Bletchley Park
Bletchley Park is an English country house and estate in Bletchley, Milton Keynes ( Buckinghamshire) that became the principal centre of Allied code-breaking during the Second World War. The mansion was constructed during the years following ...
in Milton Keynes
Milton Keynes ( ) is a city and the largest settlement in Buckinghamshire, England, about north-west of London. At the 2021 Census, the population of its urban area was over . The River Great Ouse forms its northern boundary; a tributary ...
, Buckinghamshire.
In November 2007, to celebrate the project completion and to mark the start of a fundraising initiative for The National Museum of Computing, a Cipher Challenge pitted the rebuilt Colossus against radio amateurs worldwide in being first to receive and decode three messages enciphered using the Lorenz SZ42 and transmitted from radio station DL0HNF in the ''Heinz Nixdorf MuseumsForum'' computer museum. The challenge was easily won by radio amateur
An amateur radio operator is someone who uses equipment at an amateur radio station to engage in two-way personal communications with other amateur operators on radio frequencies assigned to the amateur radio service. Amateur radio operators h ...
Joachim Schüth, who had carefully prepared for the event and developed his own signal processing and code-breaking code using Ada
Ada may refer to:
Places
Africa
* Ada Foah, a town in Ghana
* Ada (Ghana parliament constituency)
* Ada, Osun, a town in Nigeria
Asia
* Ada, Urmia, a village in West Azerbaijan Province, Iran
* Ada, Karaman, a village in Karaman Province, ...
. The Colossus team were hampered by their wish to use World War II radio equipment, delaying them by a day because of poor reception conditions. Nevertheless, the victor's 1.4 GHz laptop, running his own code, took less than a minute to find the settings for all 12 wheels. The German codebreaker said: "My laptop digested ciphertext at a speed of 1.2 million characters per second—240 times faster than Colossus. If you scale the CPU frequency by that factor, you get an equivalent clock of 5.8 MHz for Colossus. That is a remarkable speed for a computer built in 1944."
The Cipher Challenge verified the successful completion of the rebuild project. "On the strength of today's performance Colossus is as good as it was six decades ago", commented Tony Sale. "We are delighted to have produced a fitting tribute to the people who worked at Bletchley Park and whose brainpower devised these fantastic machines which broke these ciphers and shortened the war by many months."
Other meanings
There was a fictional computer named ''Colossus'' in the 1970 film '' Colossus: The Forbin Project'' which was based on the 1966 novel ''Colossus
Colossus, Colossos, or the plural Colossi or Colossuses, may refer to:
Statues
* Any exceptionally large statue
** List of tallest statues
** :Colossal statues
* ''Colossus of Barletta'', a bronze statue of an unidentified Roman emperor
* ''Col ...
'' by D. F. Jones. This was a coincidence as it pre-dates the public release of information about Colossus, or even its name.
Neal Stephenson's novel ''Cryptonomicon
''Cryptonomicon'' is a 1999 novel by American author Neal Stephenson, set in two different time periods. One group of characters are World War II-era Allied codebreakers and tactical-deception operatives affiliated with the Government Code an ...
'' (1999) also contains a fictional treatment of the historical role played by Turing and Bletchley Park.
See also
* History of computing hardware *List of vacuum-tube computers
Vacuum-tube computers, now called first-generation computers, are programmable digital computers using vacuum-tube logic circuitry. They were preceded by systems using electromechanical relays and followed by systems built from discrete transi ...
* Manchester Baby
The Manchester Baby, also called the Small-Scale Experimental Machine (SSEM), was the first electronic stored-program computer. It was built at the University of Manchester by Frederic C. Williams, Tom Kilburn, and Geoff Tootill, and ran its ...
* Z3
* Z4
Footnotes
References
* * * in * * * * * * in * in * in * in * * in * Updated and extended version of ''Action This Day: From Breaking of the Enigma Code to the Birth of the Modern Computer'' Bantam Press 2001 * in * * in * * * ** ** ** ** * * * * * * in * * describes the operation of Colossus in breaking Tunny messages * in * * inFurther reading
* * A short film made by Google to celebrate Colossus and those who built it, in particular Tommy Flowers. * – A detailed description of the cryptanalysis of Tunny, and some details of Colossus (contains some minor errors) * :::A guided tour of the history and geography of the Park, written by one of the founder members of the Bletchley Park Trust * * * – Comparison of the first computers, with a chapter about Colossus and its reconstruction by Tony Sale. * A slender (20-page) booklet, containing the same material as Tony Sale's website (see below) *External links
Early computer development
The National Museum of Computing (TNMOC)
*
TNMOC: The 75th anniversary of the first attack
Contains a great deal of information, including: *
*
**
**
**
**
A detailed tour of the replica Colossus – make sure to click on the "More Text" links on each image to see the informative detailed text about that part of Colossus *
IEEE lecture
– Transcript of a lecture Tony Sale gave describing the reconstruction project
BBC news article reporting on the replica Colossus
BBC news article: "Colossus cracks codes once more"
BBC news article: BBC news article: "Bletchley's code-cracking Colossus" with video interviews 2010-02-02
with much information and links to recently declassified information
Was the Manchester Baby conceived at Bletchley Park?
*
online virtual simulation of Colossus
{{Mainframes 1940s computers Early British computers Bletchley Park Cryptanalytic devices Military computers Vacuum tube computers World War II British electronics English inventions Computer-related introductions in 1943 Computer-related introductions in 1944 Computer-related introductions in 1945 Serial computers